Extending high-resolution medical imaging from a secure PACS workstation to a conference room often results in a mess of cables, unreliable connections, and major security risks. This ad-hoc approach creates friction and compromises data integrity.
KVM-over-IP links PACS workstations to conference displays only when pixels, control, and identity are cleanly separated, latency stays deterministic, and access is segmented by role/room. Pair fixed multiview templates with resilient endpoints (4K60, proper EDID, USB-HID backfeed) and audited switching. The result: secure, low-friction sharing from reading room to boardroom—without sacrificing image fidelity or control.
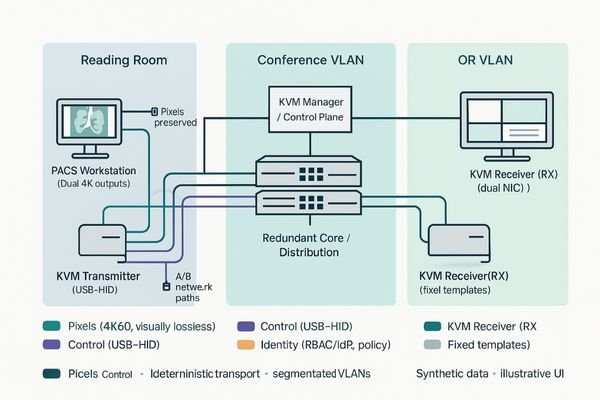
The goal of sharing a radiologist’s screen with a multidisciplinary team in a conference room or an operating theater is simple: provide seamless, real-time access without compromising image quality, security, or usability. KVM-over-IP technology1 promises to deliver this, but a poorly planned deployment can introduce unacceptable latency, access control loopholes, and frustrating technical glitches. A successful integration is not about just connecting boxes; it is a discipline that requires a clear architectural strategy2 for separating data streams, enforcing access policies, and validating performance from end to end.
KVM-over-IP from reading room to boardroom: what actually travels
Many KVM systems are treated like a simple video cable extension. This oversimplification ignores the complex data streams being transmitted, leading to unpredictable lag, control issues, and serious security vulnerabilities.
Successful KVM-over-IP design begins by separating three distinct streams: pixels (video), control (USB-HID), and identity (access rights). Blurring these streams is the primary cause of latency, desynchronization, and unintended access.
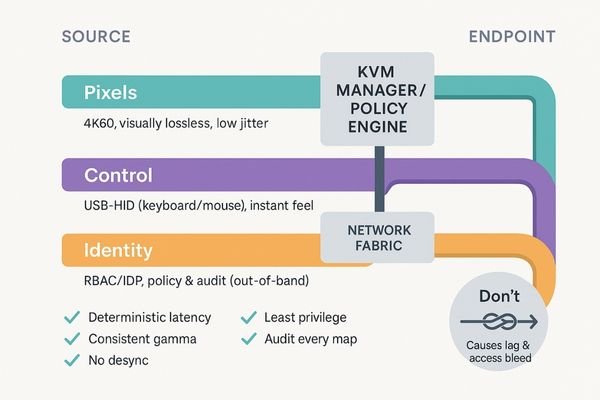
When architecting a KVM-over-IP system3 to connect a PACS reading room to a conference display, the first step is to recognize that you are not just sending "video." You are managing three independent data streams, and each has unique requirements. The first stream is the pixels—the high-resolution video data4 itself. This requires predictable, high-bandwidth transport with low, consistent latency. The second stream is control, which includes the USB-HID (Human Interface Device) data for keyboard and mouse actions. This needs to be extremely responsive, with near-instantaneous feedback to feel natural. The third and most critical stream is identity, which governs who is allowed to control what, from where. This stream must be managed by the control plane and should never "hitch a ride" with the pixel data. I have consistently seen that when these three streams are not kept distinct at both a network and system level, teams suffer from mystery lag, mouse cursors that become desynchronized from the display, or—in the worst-case scenario—unauthorized users gaining control of a workstation from another room.
Latency, fidelity, and control: the non-negotiable budgets
The pursuit of "lossless" image quality often leads to systems with variable, high latency. This makes interactive tasks like scrolling through a CT stack or manipulating a 3D model nearly impossible.
The glass-to-glass latency budget for interactive tasks is non-negotiable: it must remain under 100 ms. Stable 4K60 with consistent gamma and a visually lossless profile is superior to a high-bitrate stream with unpredictable delays.
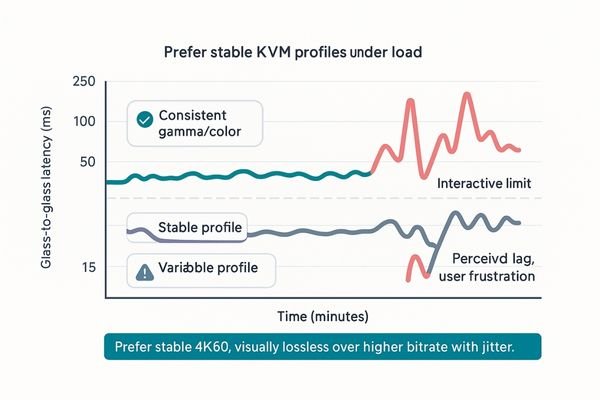
In any system that involves remote control, latency budgets are brutally honest. If the total time from a mouse movement at the conference table to the corresponding cursor movement on the screen (glass-to-glass latency) exceeds 100 milliseconds, users will perceive a disconnect. They will lose confidence in the system and resort to inefficient workarounds. Therefore, when configuring a KVM system, I prioritize deterministic latency5 over chasing the highest possible bitrate. A visually lossless compression6 profile that guarantees a consistent frame delivery rate is far more usable for clinical review than an exotic "mezzanine" level codec that looks perfect but drifts under network load. This is especially true for reading fine details on a diagnostic display like the MD85CA. In daily practice, a stable 4K60 video stream that maintains consistent gamma and color accuracy always wins against sporadic bursts of pristine but delayed frames. The system must feel responsive and predictable every single time.
| Parameter | Budget/Target | Rationale |
|---|---|---|
| Glass-to-Glass Latency | < 100 ms | Threshold for perceptible lag in interactive tasks. |
| Image Fidelity | Visually Lossless @ 4K60 | Balances quality with the need for deterministic, low-latency transport. |
| Color/Gamma Consistency | Factory Calibrated/DICOM | Ensures images look the same at the source and destination. |
Access segmentation that works: roles, VLANs, and source whitelists
The "anything-anywhere" matrix is a common selling point for KVM systems, but it often creates chaos. Unrestricted access leads to users accidentally disrupting sessions in other rooms or accessing sensitive data.
Effective access segmentation combines role-based permissions, room-scoped VLANs, and source whitelists. Pairing these rules with fixed, task-based multiview templates prevents improvisation and enforces policy through workflow.
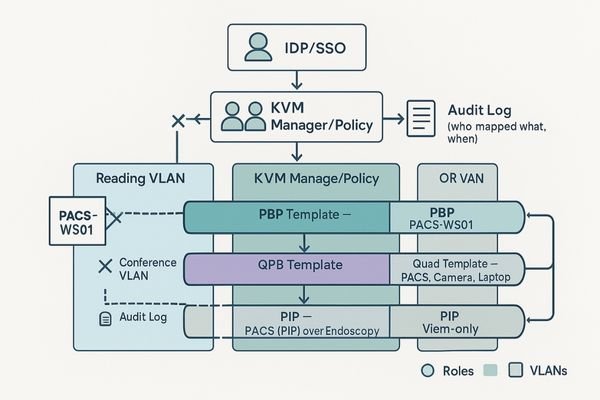
Access segmentation is not a feature to be enabled with a single checkbox; it is a fundamental aspect of workflow design. The dangerous fantasy of an "anything-anywhere" matrix, where any user can pull any source to any screen, must be replaced with a structured, policy-driven approach. A robust segmentation strategy has three layers. First, Role-Based Access Control (RBAC)7 defines permissions based on user type (e.g., a radiologist has full control, while a trainee has view-only access). Second, network-level VLANs8 isolate traffic, ensuring that devices in the conference room are on a separate logical network from the secure PACS reading room. Third, source whitelists explicitly define which workstations can be accessed from which endpoints. I have learned to make this security model intuitive by pairing it with fixed, obvious multiview templates on the destination display. For example, a large conference display like the MS550P can be configured with a permanent A/B layout for comparing a live PACS feed with a presentation. When policy is embedded in the workflow template, security and usability cease to be enemies.
Endpoint realities: EDID, 4K60, USB-HID backfeed, and fixed multiview
The perfect KVM transport system can be defeated by a poorly chosen endpoint. A consumer-grade TV in a conference room may not correctly report its capabilities or handle professional signals reliably.
The endpoint display is the last-mile decider. It must have correct EDID for 4K60 negotiation, support clean USB-HID backfeed, and offer fixed multiview modes to handle signal loss gracefully.
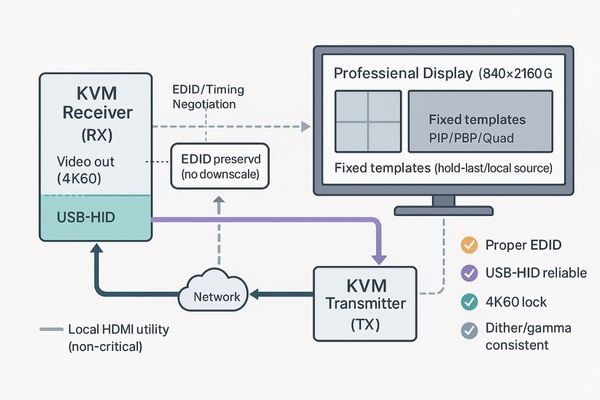
The KVM network can deliver a perfect signal, but the entire experience is decided at the "last mile"—the endpoint display in the conference room or OR. Several realities at the endpoint can make or break the system. The display’s EDID (Extended Display Identification Data)9 is critical; if it is incorrect or poorly implemented, the KVM encoder may fail to negotiate the proper 4K60 timing, resulting in a blank screen or a downgraded resolution. The display must also support a clean USB-HID backfeed path, ensuring that keyboard and mouse commands sent from the receiver are reliably transmitted back to the source workstation. I also insist on endpoints that have built-in, fixed multiview capabilities (PIP/PBP)10. This is a powerful resilience feature. For instance, if the KVM stream to a large surgical monitor like the MS322PB is used alongside a local camera feed, having the monitor manage the multiview layout means a failure of one stream does not black out the entire screen. The endpoint is not a passive component; it is an active participant in the system’s success.
Resilience and audit: failover paths and who touched what, when
When a KVM system fails, the immediate question is "what happened?" without clear failover paths and an audit trail, the result is frantic cable-swapping and unproductive finger-pointing.
Resilience requires boring redundancy: dual network paths and a simple, local bypass that staff can activate in under 10 seconds. An audit trail detailing "who mapped what, when" is just as vital for fast recovery.
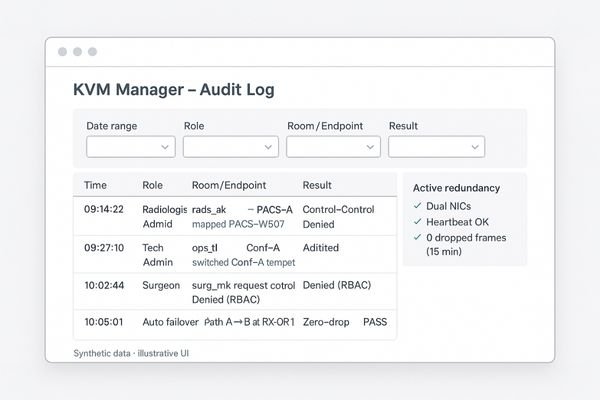
A truly resilient KVM system is prepared for failure. This preparation has two components: technical redundancy11 and procedural clarity. Technical redundancy should be straightforward and, frankly, boring. This means using endpoints with dual network interface cards (NICs) connected to separate network switches, creating redundant signal paths. It also means providing a known-good local fallback, such as a direct HDMI bypass connection that staff can invoke with a single button press or cable swap in less than ten seconds. Just as vital is the ability to audit the system’s use. The KVM management software must maintain a clear, human-readable narrative log that answers the question: "Who mapped which source to which endpoint, and when?" On the day something goes wrong—and it will—this audit trail12 is the difference between a quick, targeted recovery and a prolonged outage filled with guesswork. This level of resilience and accountability is essential whether the endpoint is a primary diagnostic monitor like the MD120C or a remote collaboration display.
Conclusion
A well-designed KVM-over-IP system transforms sharing medical images from a high-friction, insecure task into a seamless, reliable, and secure extension of the clinical workflow. 🔗
👉 For expert insights and Reshin’s KVM-over-IP display solutions, contact martin@reshinmonitors.com.
-
Understanding KVM-over-IP technology is crucial for ensuring seamless access and high-quality image sharing in medical settings. ↩
-
Exploring architectural strategies can help avoid common pitfalls and ensure successful technology integration. ↩
-
Understanding KVM-over-IP systems can enhance your knowledge of remote access technology and its applications. ↩
-
Exploring the benefits of high-resolution video data can help you appreciate its importance in various applications, including medical imaging. ↩
-
Understanding deterministic latency is crucial for optimizing remote control systems and ensuring user confidence. ↩
-
Exploring visually lossless compression can enhance your knowledge of efficient video streaming and improve system performance. ↩
-
Understanding RBAC is crucial for implementing effective access control in any organization, enhancing security and compliance. ↩
-
Exploring VLANs can help you learn how to isolate network traffic, improving security and performance in your IT infrastructure. ↩
-
Understanding EDID is crucial for ensuring optimal display performance and avoiding resolution issues. ↩
-
Exploring multiview capabilities can reveal how they improve user experience and system resilience in critical environments. ↩
-
Understanding technical redundancy is crucial for building resilient KVM systems that can withstand failures. ↩
-
Exploring the importance of an audit trail can enhance your knowledge of system accountability and recovery processes. ↩



